Securing sections in Web.Config
For ASP.Net applications, developers usually store lots of configuration data in the Web.Config, some of such settings can contain secured information such as connection strings, email settings, proxy settings etc. Storing credential information in Web.Config as plain text is a threat as this could lead to leak the information. Though the web server will not render web.config files to the visitors, you need to see there could be users, such as system administrators, back up operators, etc who have access to your server’s file system. Exposing secured information for such users is a threat and you need to protect your configuration data. The solution is to encrypt the sections in Web.Config and thankfully ASP.Net offers out of the box support for encrypting and decrypting the connection string placed inside Web.Config.
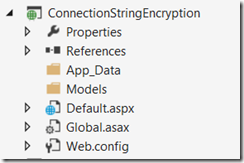
In this article I am going to demonstrate, how to encrypt/decrypt the connection string section in Web.Config, you can follow the same concepts to encrypt any other section in web.config. For the purpose of the article, I created an ASP.Net empty web application and added a default.aspx file. The project in solution explorer looks as follows.
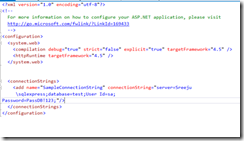
For the purpose of this article, I created a test database and a table named “test”, and added some sample data to the table. In the web.config I added the connection string. My web.config looks as follows.
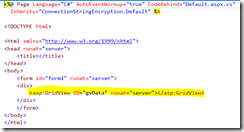
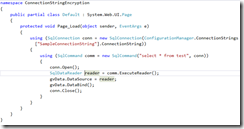
I added a grid view to the default.aspx page. The source for aspx and aspx.cs is given below.
Default.aspx
Default.aspx.cs
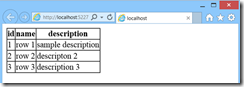
When I rab the page, I got the below output.
This looks so simple, now I am going to encrypt the connection string, in the Web.Config. In order to encrypt the connection string, you need to use the aspnet_regiis tool, which is available under the following location.
%WinDir%\Microsoft.NET\Framework\<versionNumber>
For encrypting the connection string using aspnet_regiis tool, the following parameters are avaialble with the aspnet_regiis
The -pe switch specifies the configuration section to encrypt.
The -pef switch specifies the configuration section to encrypt and allows you to supply the physical directory path for your configuration file.
The -app switch specifies your Web application's virtual path. If it is a nested application, you need to specify the nested path from the root directory; for example, "/test/aspnet/MachineDPAPI".
The -prov switch specifies the provider name.
For the purpose of this demonstration, I prefer to use –pef option as I can pass a source Web.Config, so I can easily encrypt the web.config, then copy it to my application.
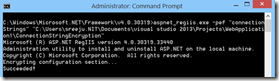
Open command prompt as administrator, then navigate to the path where you installed asp.net. Now enter the aspnet_regiis.exe, mention connectionStrings as the section and then specify the path to your Web.Config.
aspnet_regiis.exe -pef "connectionStrings" "C:\ConnectionStringEncryption"
Once the command is executed successfully, you will see the succeeded message in the Visual Studio.
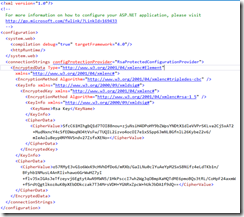
Now check the connection string in the web.config, you will see it is encrypted, Hurray!
From a developer perspective, you are not required to change anything as ASP.Net will handle the decryption of the connection string. I just ran the application again and received the same output as above. The whole purpose of creating the default.aspx page was to show you how simply ASP.Net handles the encryption and decryption without worrying the developer. When you move the site to production, you can decide what sections of your Web.Config needs to be encrypted, and do that with out changing even single line in your code.
In this article we have seen how to encrypt connection string, now what if you need to encrypt other sections, the answer is simple, just specify the path of your settings in the Aspnet_regiis command. For e.g. to encrypt the smtp settings, just use the below.
aspnet_regiis.exe -pef "system.net/emailSettings/smtp" "C:\ConnectionStringEncryption"
Summary
ASP.Net makes it easy to protect your configuration data easily without adding any hassles to the developer. As a developer you should not worry about the encryption/decryption of your settings as ASP.Net will take care of this.
Further reading:
http://msdn.microsoft.com/en-us/library/zhhddkxy%28v=vs.100%29.aspx